Executive Summary
RWS requires an integrated XDR platform with 24x7x365 MXDR operations to strengthen cybersecurity operational resilience, accelerate detection-to-containment, and meet strict governance and regulatory expectations. For this requirement, SoftwareOne has partnered with Armor Defense, a tech-enabled services company providing Managed Detection and Response (MDR) services with unified threat visibility, faster response, and audit-ready operations.
Coverage Scope
Base (mandatory)
Core endpoint/server protection and EDR, XDR correlation and incident lifecycle management, integrations and automation, plus vulnerability capability requirements as defined in scope.
Optional modules
Email Security, Network/NDR, Identity Protection, Mobile, IoT/OT, Additional Cloud Workloads (e.g., AliCloud) and AI/GenAI Security supported without re-architecture if activated later.
Implementation Approach and Timeline
Foundation
Architecture/design, platform foundation, integrations and acceptance planning.
Rollout
Ring-based rollout and migration/onboarding with stabilization and governance.
Operations
Steady-state 24x7x365 MXDR operations and continuous improvement.
Milestones: Commissioning before 1 Jun 2026. Full onboarding and operational before 31 Dec 2026.
What RWS Gets
Reduced Business Risk
Faster detection and containment via unified incident correlation and governed response playbooks across endpoint, identity, email, and cloud.
24/7/365 Singapore-Based SOC
Monitoring by local L2/L3 analysts who understand APAC threats. Global follow-the-sun coverage for other activities like threat intelligence, detection engineering and more.
Lower Operational Burden
Consolidated security operations with standardized workflows, reporting, and continuous tuning to reduce noise.
Extreme Microsoft Security Depth
Full M365 E5 integration, maximizing your existing investment with expert human oversight and response.
Rapid Incident Response
15-minute response SLA for critical incidents with pre-approved containment actions.
AI-Augmented Detection
Armor AI accelerates investigations combined with curated threat intelligence for proactive hunting.
Stronger Assurance
Evidence-grade auditability and support for regulatory and internal compliance obligations.
Phased Delivery
Controlled migration with coexistence validation and rollback planning to minimize disruption.
Armor Key Differentiators
No Walled Gardens. Challenging the Industry.
Armor isn't another security vendor with a closed ecosystem. We deliver a flexible framework where you never lose control or visibility of your risk posture. We orchestrate your existing investments into a coherent security strategy - fully adaptable as your partners and needs evolve.
Armor Dash
Executive Security Dashboard
Unified visibility across all security vendors, tools, and GRC platforms. AI-powered insights in plain English. Financial risk quantification for executive level conversations.
Armor Nexus
Incident Operations Platform
Unified XDR platform with AI-powered detection, automated playbooks, and real-time SOC collaboration. Bi-directional sync with your existing SIEM and ITSM systems.
No Black Box
All detection rules, tuning, and automations created for RWS are fully transparent, RWS-owned, and transferable. Your security IP stays with you.
Noise-Free Security
Armor MDR filters irrelevant alerts and reduces noise - we value your time as much as you do.
True Partnership
Co-managed approach integrates seamlessly with your team as a genuine extension, not an add-on.
Human-AI Synergy
AI-driven detection combined with expert human analysis for precision and speed.
Compliance Built-In
Compliance-ready reports and dashboards help meet regulatory requirements effortlessly.
Custom Playbooks
Tailored response workflows aligned to your business processes - not generic, one-size-fits-all.
Bi-directional ITSM Sync
Incidents flow seamlessly between Armor and RWS's existing SIEM/ITSM systems without disrupting your established workflows.
Armor Reactor
Data security for the AI era - discover, monitor, and govern your organization's AI ecosystem with automated playbooks and privacy controls.
Platform Differentiator
Microsoft Security: A Unified Ecosystem vs. Point Solutions
While competitors offer individual tools, Microsoft delivers an integrated security ecosystem where every component shares intelligence, correlates signals, and responds as one unified platform.
Microsoft Security Ecosystem
Integrated Platform- Native Integration - Defender XDR, Sentinel, Entra ID, Intune, and Purview share a common data fabric
- Unified Correlation - Cross-domain signals from endpoints, identity, email, and cloud automatically correlate into incidents
- Single Console - One portal for detection, investigation, and response across all attack surfaces
- Shared Threat Intelligence - 100+ trillion signals daily powering all components simultaneously
- Automated Response - Native playbooks span identity, endpoint, and cloud without API bridges
- License Efficiency - M365 E5 bundles comprehensive security, reducing total cost of ownership
Point Solution Approach
Palo Alto / CrowdStrike / Splunk- Integration Tax - Each tool requires custom connectors, API maintenance, and data normalization
- Manual Correlation - Analysts must pivot between consoles to piece together attack chains
- Multiple Consoles - Separate portals for EDR, SIEM, identity, and cloud create context switching
- Siloed Intelligence - Threat data locked within each vendor's ecosystem
- SOAR Dependency - Requires separate orchestration layer to coordinate cross-tool response
- Stacked Licensing - Each capability requires separate procurement and renewal cycles
The RWS Advantage: By consolidating on Microsoft Security with Armor MDR, RWS gains ecosystem-native detection and response that eliminates integration complexity while reducing vendor management overhead.
Company Profile
SoftwareOne
SoftwareOne is a leading global software and cloud solutions provider, helping organizations optimize their software portfolios and accelerate cloud transformation. With operations in 90+ countries and 9,000+ employees, we combine local expertise with global scale.
SoftwareOne Certifications
ISO 27001
Information Security Management
SOC 2 Type 1
Security, Availability, Confidentiality
CSA
SoftwareOne Pte LtdUEN: XXXXXXXXXX
Lic. ID: XXXXXXXXXXXXXXXXXX
Armor

Armor is a cloud-native managed security provider recognized by Frost & Sullivan as a leader in Managed Detection and Response. Our platform combines advanced threat detection, expert security analysts, and automated response capabilities to protect organizations across cloud, hybrid, and on-premises environments.
"Armor's MDR platform delivers unified visibility across cloud and on-premises environments with 24/7 expert monitoring and rapid response capabilities."
Lucas Ferreyra, Senior Industry Analyst - Frost & Sullivan
Armor Certifications
ISO 27001
Information Security Management
SOC 2 Type II
Security, Availability, Confidentiality
PCI DSS
Payment Card Industry Compliance
HITRUST CSF
Healthcare Security Framework
Data Privacy Framework
US-EU Data Transfer Compliance
PDPA
Singapore Personal Data Protection
GDPR
EU General Data Protection Regulation
CSA
ARMOR DEFENSE ASIA PTE. LTD.UEN: 202222526H
Lic. ID: CS/SOC/C-2022-0154R
Team Certifications
CISSP
Certified Information Systems Security Professional
CISA
Certified Information Systems Auditor
CRISC
Certified in Risk and Information Systems Control
GXPN
GIAC Exploit Researcher
OSCP
Offensive Security Certified Professional
OSCE
Offensive Security Certified Expert
OSED
Offensive Security Exploit Developer
OSEP
Offensive Security Experienced Penetration Tester
OSWE
Offensive Security Web Expert
+ Dozens More
Industry certifications across the team
Better Together
Deep expertise. Zero overlap. One team.
SoftwareOne
Cloud + AI + IT
We build, optimize, and manage your digital infrastructure.
Armor
Cybersecurity
We protect it - 24/7, across every environment.
For RWS: No coordination overhead. No finger-pointing. One unified team accountable for outcomes.
Understanding RWS Requirements
Based on the RFQ specifications and our discussions, we understand RWS seeks a comprehensive MXDR solution that addresses the following core requirements:
Interpretation of RWS Security and Operational Requirements
| RWS Objective | Our Understanding |
|---|---|
| Scope & outcomes | RWS seeks an integrated EPP/EDR/XDR platform with Managed XDR (MXDR) that strengthens detection, investigation, response and operational resilience across servers, workstations/laptops, persistent & non-persistent VDI, and containerized workloads, delivered over 3 + 1 + 1 years. |
| Platform capabilities | The platform must use a single lightweight agent and a single cloud-native console, support RBAC, provide rich telemetry and hunt/search, deliver behavioural analytics, UEBA, automated playbooks, and cross-domain orchestration, including ransomware rollback. |
| Security operating model | Day-2 MXDR runs 24x7x365 fully within the RWS tenant with named, least-privilege accounts (MFA, JIT/PAM, IP allow-listing); Singapore-based L2/L3 escalation within 2 hours. |
| Performance, SLOs & SLAs | Target SLOs include endpoint event searchable in 15s, identity/email in 60s, cloud audit in 120s; action execution in 30s; console uptime 99.9%; false-positive rate 2% monthly. Threat-hunting SLAs define ack in 4h, critical IoC sweep in 4h, standard IoC in 24h, complex hunts in 72h, and hunt report in 24h post-completion. |
| Integration & environment fit | Native integration with Microsoft Entra ID (AD) SSO, IDAS, SIEM/CLM/data lake, ITSM, email, firewalls/NDR, cloud audit (Azure first), with alignment to RWS standard tech stacks. |
| Compliance & auditability | The service must support PDPA-aligned controls, immutable evidence, evidentiary bundles, SLA telemetry (MTTD/MTTR), change control, and certification posture. |
RWS's objective is to uplift cybersecurity operational resilience through an integrated EPP/EDR/XDR platform with 24x7x365 MXDR operations, delivered with a controlled migration from incumbent tooling and measurable operational outcomes.
We understand RWS currently operates Splunk as the SIEM platform with Cybereason XDR for endpoint detection and response. Our implementation approach specifically addresses coexistence during transition, ensuring zero protection gaps during cutover and preserving operational continuity. The migration plan includes parallel operation periods, validation gates, and coordinated retirement of incumbent agents only after full Microsoft Defender XDR coverage is confirmed.
RWS Security & Operational Requirements
Unified Platform
Single-agent / single-console design with cloud-native telemetry correlation, strong anti-tamper controls, and controlled rollout.
Unified Threat Visibility
Consolidated view across endpoints, identity, email, cloud workloads, and applications through Microsoft Defender XDR integration.
Scale & Environment
Approx. 7,500 agents across endpoints and servers (hybrid estate), with Prod/UAT/SIT environments and cross-domain telemetry ingestion.
SOC/MXDR Operating Model
24x7x365 MXDR operations with Singapore-based L2/L3 escalation within 2 hours.
Expert-Led Response
24/7 human analyst coverage for threat triage, investigation, and response - not just automated alerts.
Operational Integration
Seamless integration with RWS's existing SIEM, ITSM, and security workflows without disruption.
Training & Knowledge Transfer
Role-based training for SOC, IT Ops, and management, plus quarterly workshops for capability uplift.
Compliance Alignment
Support for regulatory requirements including data residency, audit trails, and reporting.
Key Challenges and Risk Areas Addressed by the Proposed Solution:
| RWS Challenge | Right-fit Solution |
|---|---|
| Migration and co-existence with incumbent EPP/EDR | Phased deployment, policy parity and structured rollback plans |
| Hybrid/on-prem + cloud telemetry normalization | Cloud-based scalable architecture. Custom or built-in parsers to normalize data. |
| Noise & false positives reduction | Armor Nexus platform provides full visibility into MDR operations including False Positive reduction overtime. |
| Server-safe containment guardrails | Approval gates in playbooks, pre-approved high-severity actions catalog, exception lists. |
| Regulatory reporting & audit trails | Armor Nexus dashboard provides compliance-ready reporting and immutable audit trails. |
| Singapore-based L2/L3 escalation and Project Manager | Armor Local MDR experts will assist when needed. |
| xAI requirements | Microsoft Security Copilot and Armor Nexus portal provide transparency, feature importance, confidence, auditability |
Assumptions & Dependencies
- June deadline achievable only if project awarded in January 2026
- Devices updated and all pre-requisites met before MDE onboarding
- Armor will provide instrumentation, dashboards, and monthly reporting of SLO-style metrics under agreed volumes and conditions but does not warrant or commit to specific SLO thresholds. Only service SLAs (response/resolution/availability per Section 17) are contractually binding.
- ORT/Commissioning and PGP completion will be based on functional correctness, defect exit criteria, documentation, and SLA process readiness; performance observations will be reported but not guaranteed as SLO commitments
- For XDR implementation, the platform shall be fully operational
Supporting RWS Business Priorities
RWS is executing one of Asia's largest hospitality transformations with the RWS 2.0 expansion. New attractions, hotels, and digital experiences rolling out through 2030 will significantly expand the technology footprint requiring protection. This proposal leverages RWS's existing Microsoft investments, extends them with Armor Nexus for operational transparency, and provides managed XDR expertise to scale security alongside business growth.
Scaling Security with Business Growth
As RWS 2.0 brings new properties, attractions, and guest systems online, the security perimeter expands with each phase. Construction timelines and vendor access add complexity that traditional security teams struggle to absorb.
How this proposal helps:
- Microsoft Defender XDR provides unified visibility across endpoints, identity, email, and cloud from a platform RWS already uses, eliminating new tool adoption during critical expansion phases
- Armor Nexus delivers a single operational view as new systems come online, with AI-powered triage that scales detection capacity without proportional headcount growth
- Armor's managed service model absorbs the operational complexity of expanding environments, allowing RWS IT to focus on business-critical initiatives rather than security operations scaling
Protecting Digital Experience Investments
Guest-facing digital initiatives depend on infrastructure that must remain secure and available. High guest volumes mean any security incident affecting digital systems has immediate operational and reputational impact.
How this proposal helps:
- Microsoft Defender XDR correlates threats across the full Microsoft ecosystem, detecting attacks that span endpoints, identity, and cloud workloads before they impact guest-facing systems
- Proactive threat hunting identifies risks to guest-facing infrastructure before they become incidents, while pre-approved containment actions enable immediate response without waiting for change approval during an active threat
- Armor Nexus AI-augmented triage delivers 8x faster analysis, reducing mean time to containment for threats targeting operational systems
Governance and Regulatory Visibility
Singapore's regulatory environment requires demonstrable security governance with audit-ready documentation and clear accountability. Security operations must be transparent and defensible.
How this proposal helps:
- Armor Nexus transforms the traditional "black box" MDR model into a fully transparent partnership with real-time visibility into every detected threat, SOC action, and incident status
- Microsoft Defender XDR integration with Sentinel provides compliance-ready dashboards and immutable audit trails that satisfy regulatory scrutiny
- Structured reporting through weekly, monthly, and quarterly reviews creates the governance cadence regulators expect
Why this matters for RWS: Armor accelerates time-to-value from Microsoft security investments while removing the operational burden from RWS IT. As RWS 2.0 demands focus on guest experience, new attractions, and operational excellence, Armor provides mature security operations that scale with the business and evolve with the threat landscape.
Implementation Approach
Our phased implementation methodology ensures minimal disruption to RWS operations while accelerating time-to-value. Each phase builds upon the previous, with clear milestones and success criteria.
Validation
Planning
Coexistence
Cutover
Full Operations
Outcome
Management Milestones
- Define PoC scope and success criteria
- Execute PoC in constrained environment
- Validate results are correct and reproducible
- Environment discovery and critical assets
- Solution architecture design
- Project plan and risk log
- Roles and responsibility mapping (RACI)
- Rollout ring design
- Draft test plans (SIT/UAT/ORT/DR)
- Execute SIT → UAT → Failover → HA/DR → ORT
- Defect management and test reports
- Knowledge transfer workshops
- Pilot rollout to smaller group
- Ring-based enterprise deployment
- Remove incumbent agents
- Confirm incumbent removal complete
- Transition to steady-state operations
- Operational handover documentation
Platform Key Tasks
- Verify licensing and prerequisites
- Network connectivity validation
- Environment discovery
- Device groups and RBAC design
- Workspace and connector planning
- Integration strategy for existing tools
- Map incumbent settings to Defender XDR
- Set up forwarders, connectors, subscriptions
- Set mutual EDR exclusions
- Push registry keys for passive mode
- Onboard endpoints (ring-based)
- Onboard servers (change-controlled)
- Configure dual log forwarding
- Run detection tests, verify healthy devices
- Complete endpoint migration
- Complete server migration
- Uninstall incumbent AV/EDR
- Force MDAV active and enforce policies
- Configure single log forwarding to Sentinel
- Apply ASR rules
- Enable Auto Disruption
- Enable Tamper Protection
- Enable Web/Network Protection
- Verify Microsoft best practices alignment
Service Readiness
- Understand business and regulatory requirements
- Geolocation setup and BU mapping
- Identify crown jewels and critical assets
- Map existing cybersecurity tools
- Review existing playbooks
- Use case planning & detection design
- Define autonomous vs approval-required actions
- Gap analysis against best practices
- 24x7 monitoring begins for onboarded devices
- Use case deployment
- Initial threat response capability active
- Expanding coverage as devices rollout
- Use case tuning & optimization
- Policy hardening
- Full MXDR operations active
- All endpoints under 24x7 monitoring
- All capabilities enabled
- Proactive threat hunting
This unified implementation roadmap integrates project governance, platform deployment, and managed security services into a single coordinated framework. Rather than managing three separate workstreams with independent timelines and handoffs, RWS gains visibility into how each track progresses through common stage gates—ensuring that technical readiness, operational preparedness, and business outcomes remain aligned at every milestone.
The approach is deliberately structured around coexistence and controlled transition. Allowing the XDR platform to coexist with incumbent tooling during Stage 3 significantly reduces migration risk—detection coverage remains continuous, rollback paths stay available, and teams can validate behavior in production conditions before committing to cutover. MXDR services activate at the point of commissioning approval—not after full deployment—meaning RWS benefits from 24x7 threat monitoring from the earliest transitioned workloads through the complete and final cutover.
Why this matters for RWS: Security transformation projects frequently stall or fail when platform deployment, service enablement, and governance operate on disconnected tracks. This integrated model compresses time-to-protection, reduces execution risk, and ensures that every stage gate delivers measurable business value—from validated solution fit through to maximum security posture. For RWS, this means faster realization of your security investment, continuous protection throughout the transition, and a clear line of sight from technical activity to operational resilience.
Implementation Timeline
The implementation follows a gated stage approach across three parallel workstreams. Project Management establishes governance, testing protocols, and deployment controls. The XDR Platform track handles technical deployment from tenant configuration through agent rollout and legacy retirement. The MXDR Service track activates threat monitoring capabilities progressively, beginning with use case planning and culminating in 24x7 managed detection and response.
Infrastructure as Code and Security as Code practices drive the platform deployment, enabling rapid provisioning with consistent, repeatable configurations at enterprise scale. Critical dependencies are sequenced to minimize risk: proof-of-concept validation precedes architecture commitment, commissioning approval gates service activation, and ring-based deployment allows controlled rollout with rollback capability at each stage.
Why this matters for RWS: Time-to-value is weeks, not months. RWS gains 24x7 threat monitoring by week 10 while enterprise rollout continues in parallel. Each stage gate validates success before proceeding, delivering predictable outcomes with controlled risk throughout the transition.
Delivery Model | Implementation
The Implementation delivery model illustrates Armor and SWO's structured approach to deploying Microsoft Defender XDR for RWS. This framework is designed to ensure that desired security outcomes are achieved while keeping the implementation on track through disciplined stage-gate execution and continuous governance oversight.
Validation
Planning
Coexistence
Cutover
Full Operations
Service Management & Governance
Service Delivery Leadership
At the top of the model, the Armor Platform & Security Team leads delivery through five sequential stages -each building upon the previous to systematically advance the deployment. Stage 1: Discovery & Validation confirms the current environment and validates requirements. Stage 2: Architecture & Planning establishes the technical blueprint and deployment strategy. Stage 3: Foundation & Coexistence implements core infrastructure while maintaining operational continuity with existing systems. Stage 4: Rollout & Cutover executes the phased deployment across RWS environments. Stage 5: Hardening & Full Operations optimizes configurations and transitions the platform to steady-state operations.
The successful completion of all five stages delivers the target outcome: a fully operational Microsoft Defender XDR platform providing comprehensive threat detection and response capabilities.
Underpinning the entire delivery is a robust Service Management & Governance framework. The RWS Project Team and Armor-SWO Project and Service Delivery Leadership collaborate through weekly operational meetings, monthly steering committee reviews, collaborative workshops, and continuous risk and issue tracking. This governance structure ensures alignment on priorities, rapid resolution of blockers, and executive visibility into progress -keeping the implementation on schedule and on target.
Why this matters for RWS: Armor and SWO's structured approach delivers confidence without complexity. Each stage validates success before proceeding, governance keeps all parties aligned, and executive oversight ensures the implementation stays on track. The result is a fully operational security platform with no surprises.
Delivery Model | Operations
The Operations delivery model illustrates how Armor provides ongoing managed detection and response services for RWS. This framework establishes clear operational touchpoints, defined responsibilities, and structured governance to ensure continuous security coverage while maintaining transparent communication between all parties.
The model operates across three integrated tiers. Technical Operations establishes the foundation where RWS ITSM integrates bidirectionally with Microsoft Defender XDR for incident ticketing and workflow automation. Armor's MDR experts -including Platform Engineers, Security Engineers, Detection Engineers, and Support Engineers -handle configuration, use case tuning, and ongoing support.
Security Operations delivers the core detection and response capability. Armor Nexus serves as the real-time MDR interface, providing AI-led enrichment, autonomous SecOps, service level tracking, executive reporting, and interactive incident management. Armor's Threat Responders and Threat Hunters work continuously to identify, investigate, and respond to security events.
Strategic Partnership ensures long-term alignment and value. Service Management & Governance provides structured touchpoints -Weekly/Monthly Service Reviews, Quarterly Executive Business Reviews, escalation management, and continuous improvement initiatives. Armor's Customer Success team, including Technical CSM, Account Executive, and Executive Sponsor, maintains strategic alignment with RWS objectives.
Why this matters for RWS: This operating model transforms security from a cost center into a strategic capability with clear accountability at every level. From daily technical operations to quarterly executive reviews, Armor serves as a dedicated partner invested in outcomes, not just activities, with transparent reporting and continuous service improvement built into the engagement.
Armor Global Delivery Locations
Armor's global delivery model combines dedicated local presence with worldwide operational reach. Singapore serves as the primary delivery location for RWS, providing regional expertise, time zone alignment, and direct APAC coverage. This local presence is reinforced by strategically positioned global facilities that enable true 24/7 follow-the-sun operations, ensuring uninterrupted security coverage regardless of regional outages, capacity demands, or global threat events.
| Region | Location | Role |
|---|---|---|
| Primary | Singapore | Primary delivery location for APAC coverage |
| Secondary | United States | Follow-the-sun coverage, disaster recovery |
| Tertiary | India | Additional capacity and redundancy |
Why this matters for RWS: A Singapore-only security operation would leave RWS vulnerable to regional outages and limited to local business hours for expert response. Armor's global footprint delivers the responsiveness of a local partner with the resilience of a multinational operation, ensuring critical security decisions happen in real-time, 24/7, regardless of where threats originate or when they strike.
Proposed Solution Architecture
Our solution leverages RWS's existing Microsoft security investments while adding Armor's expert monitoring, threat intelligence, and response capabilities.
Architecture Overview
The diagram below illustrates how security telemetry flows from RWS data sources through Microsoft Defender XDR into Armor Nexus, where our Singapore-based MDR team provides 24/7 monitoring, investigation, and response. This architecture maximizes your existing Microsoft investments while adding Armor's expert human analysis and AI-powered threat detection -with full bidirectional integration to your ITSM for seamless incident management.
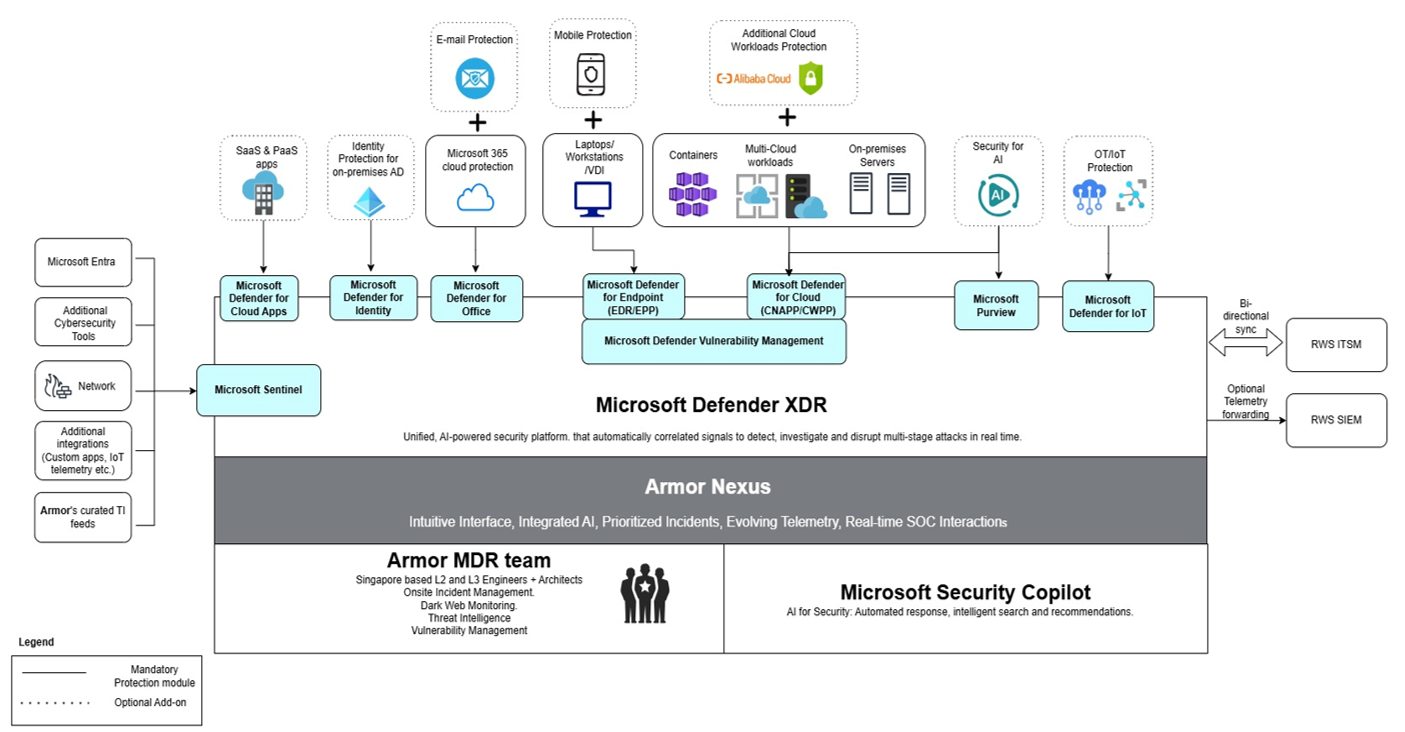
Solution Components
Microsoft Defender XDR
Your unified security platform that automatically correlates signals across endpoints, identities, email, and cloud to detect and disrupt multi-stage attacks in real-time.
Defender for Endpoint
Advanced endpoint protection with industry-first automatic attack disruption and AI-powered investigation capabilities.
- Automatic Attack Disruption: Halts ransomware in under 3 minutes with 99.99% confidence
- AI-Powered Investigation: Security Copilot reduces triage time by up to 44%
- Cross-Platform: Windows, Linux, macOS, iOS, Android, and IoT
- Threat Intelligence: 84 trillion daily signals, 10,000 experts
Defender for Identity
Real-time Active Directory monitoring that extends protection to AI agents and service accounts.
- Real-Time AD Monitoring: Detects lateral movement and compromised accounts
- Unified Identity Sensors: Widest sensor coverage for on-prem infrastructure
- Behavioral Analytics: AI detects drift in service accounts and identities
- Attack Path Analysis: Identifies and prioritizes identity attack vectors
Defender for Office 365
LLM-powered email security with sentiment analysis that detects sophisticated phishing campaigns.
- LLM-Powered Detection: 99.99% accuracy detecting attacker intent
- BEC Protection: AI identifies impersonation and compromise attacks
- Collaboration Security: Extends to Teams, SharePoint, OneDrive
- Zero-Hour Auto Purge: Removes threats post-delivery within 48 hours
Defender for Cloud Apps
Goes beyond traditional CASB with unified SSPM, app-to-app protection, and threat detection.
- Shadow IT Discovery: 1,000+ apps including GenAI with 90+ risk indicators
- SaaS Security Posture: Surfaces misconfigurations with remediation
- Integrated DLP: Native Microsoft Purview data classification
- User Behavior Analytics: Detects anomalous activity and compromises
Defender for Cloud
Cloud-native application protection platform for multi-cloud workload security.
- CSPM: Attack path analysis across Azure, AWS, and GCP
- CWPP: Runtime protection for VMs, containers, serverless
- DevSecOps: Code-to-cloud with GitHub/GitLab integration
- AI Security Posture: Purpose-built for generative AI workloads
Microsoft Sentinel
Cloud-native SIEM/SOAR with AI-powered detection and zero infrastructure to manage.
- Cloud-Native SIEM/SOAR: Rapid deployment, consumption pricing
- Fusion Detection: AI correlates signals into high-confidence incidents
- Free Log Ingestion: No cost for M365, Entra ID, Defender logs
- Security Copilot: Generative AI accelerates investigation
Why this matters for RWS: Microsoft Defender XDR represents the convergence of best-of-breed security capabilities into a unified platform, eliminating the complexity and cost of managing disparate point solutions. Each component is independently recognized as a market leader (Gartner, Forrester, IDC), yet the true value lies in their native integration: signals from endpoints, identities, email, and cloud correlate automatically to detect and disrupt sophisticated attacks that siloed tools would miss. For RWS, this translates to measurable outcomes. Organizations report up to 234% ROI, 44% faster incident response, and significantly reduced total cost of ownership through consolidated licensing, free log ingestion, and elimination of integration overhead.
Armor Nexus Platform
Nexus is Armor's unified security operations platform, providing unprecedented transparency into SOC activities, proactive threat defense, and intelligent support for complex global organizations. Launched in February 2025, Nexus delivers real-time visibility into every detected threat, SOC action, and asset status, transforming the traditional "black box" MDR model into a fully transparent security partnership.
Full SOC Transparency
Real-time window into Armor's Security Operations Center showing every action taken to neutralize threats.
- Live Activity Feed: View threat neutralization as it happens
- Hunt Findings: Detailed threat hunt results and recommendations
- Investigation Details: Full visibility into analyst workflows
- Tailored Recommendations: Environment-specific guidance
Armor Intelligence Platform (AI)
AI-driven analysis replicating expert analyst techniques at machine speed with explainable decisions.
- 95% Faster Decisions: 15 minutes reduced to 40 seconds
- 8x Faster Analysis: Accelerated investigation workflows
- Contextual Enrichment: Links vulnerabilities and campaigns
- Explainable AI: Transparent, auditable decisions
Proactive Cyber Risk Reduction
Continuously adapts defenses based on real-time intelligence and evolving attack patterns.
- Shift Left: Move earlier on MITRE ATT&CK chain
- Adaptive Defense: Real-time threat intelligence integration
- Attack Surface Reduction: Proactive vulnerability mitigation
- Impact Metrics: Visible effectiveness tracking
Incident Management & Response
Centralized incident tracking with automated escalation and remediation guidance.
- Severity Prioritization: Risk-based incident ranking
- Automated Escalation: Intelligent routing workflows
- Remediation Guidance: Step-by-step response actions
- Full Context: Complete incident timeline and evidence
Threat Hunting
AI-enabled and human-led hunting combining machine-speed detection with expert intuition.
- AI + Human: Machine speed with analyst expertise
- Proactive Searches: Find threats before incidents occur
- Environment-Specific: Tailored to your risk profile
- Detailed Findings: Actionable recommendations
Multi-Organization Support
Intelligent routing for globally distributed enterprises and complex organizational structures.
- Intelligent Routing: Segregation with unified hunting
- Global Operations: Support for distributed enterprises
- Subsidiary Management: Independent group operations
- Unified Protection: No blind spots across environment
Why this matters for RWS: Nexus eliminates the "black box" problem inherent in traditional MDR services. RWS gains complete visibility into every security action taken on their behalf, with AI-powered analysis that delivers 95% faster threat decisions while maintaining full transparency and auditability. This combination of speed, visibility, and expert human oversight translates directly into reduced risk exposure, faster incident containment, and measurable security ROI.
Armor MDR Team
Armor's Security Operations Center (SOC) combines human expertise with AI-powered capabilities to deliver enterprise-grade threat detection and response. Armor's Singapore-based team includes Security Engineers, Platform Engineers, Detection Engineers, Threat Responders, and Threat Hunters delivering specialized security operations with direct Asia-Pacific regional coverage. This dedicated local presence is backed by a globally distributed organization enabling true 24/7 follow-the-sun operational capabilities. With 15+ years protecting thousands of customers across 40+ countries and diverse industry verticals, Armor's team brings deep understanding of global threat trends and adversarial techniques to RWS's security operations. Comprehensive reporting keeps both technical teams and executive leadership informed through real-time dashboards, weekly operational summaries, and monthly executive reports.
Detection & Platform Engineering
Singapore-based engineers managing detection infrastructure, platform health, and security tool optimization with global follow-the-sun support.
- Custom Rule Development: Detection tuning specific to RWS environment and threat landscape
- ML/AI Optimization: Machine learning models tuned for multi-stage attack identification
- Platform Management: Continuous refinement of SIEM, SOAR, and XDR configurations
- Operational Dashboards: Real-time visibility into detection performance, alert volumes, and platform health
Threat Hunting & Intelligence
Proactive security specialists continuously searching for hidden threats, with fresh analysts always on duty across time zones. Hunt summaries document findings and recommendations for every threat hunt conducted.
- Hypothesis-Driven Hunting: AI-augmented investigations with 8x faster analysis
- Dark Web Monitoring: Tracks threat actor discussions targeting hospitality and gaming
- Campaign Correlation: Links indicators across endpoints, identity, and cloud
- Global Threat Intelligence: Commercial and proprietary feeds with industry context
Incident Response & Forensics
Rapid containment and expert investigation with clear escalation paths to senior specialists within minutes, regardless of time zone.
- AI-Powered Containment: Limits lateral movement within minutes of detection
- Collaborative Investigation: Works directly with RWS IT team for coordinated response
- Digital Forensics: Evidence preservation, chain of custody, and detailed reconstruction
- Remediation Guidance: Step-by-step instructions with post-incident reports documenting root cause and lessons learned
Vulnerability Management
Expert analysis and prioritization of vulnerability data from Microsoft Defender to guide remediation efforts.
- Defender Integration: Leverages Microsoft Defender Vulnerability Management scanning data
- Risk-Based Prioritization: Focuses remediation on exploitable, high-impact vulnerabilities
- Contextual Analysis: Correlates vulnerabilities with active threat campaigns
- Risk Reporting: Prioritized remediation recommendations with exploitability context and risk reduction metrics
Why this matters for RWS: Every hour of undetected threat activity increases breach costs and business disruption. Armor's MDR team delivers 95% faster threat decisions through AI-augmented analysis while human expertise ensures precision for complex attacks. With a Singapore-based team providing regional responsiveness and global 24/7 coverage, RWS gains continuous protection without the $2-4M annual cost of building equivalent in-house capabilities. This translates directly into reduced risk exposure, faster recovery, and measurable security ROI.
Microsoft Security Copilot
Microsoft Security Copilot empowers RWS's internal IT and security staff to operate as effective co-management partners alongside Armor's expert SOC team. By transforming complex security data into natural language insights, Security Copilot bridges the communication gap between Armor's security specialists and RWS's operational staff, enabling more productive collaboration during incident response and strategic planning. Combined with Armor's Intelligence Platform (AIP), which delivers plain-language threat explanations and transparent decision rationale, RWS staff gain consistent, understandable context from both platforms. This enables RWS to understand Armor's recommendations, ask informed questions, and participate meaningfully in security decisions. With 35% productivity gains and the ability to answer security questions 44% more accurately, Security Copilot ensures RWS can fully leverage Armor's expertise while maintaining visibility into their security posture.
Incident Investigation & Summarization
AI-powered incident summaries that help RWS staff understand and follow Armor's investigation findings.
- Attack Summarization: Plain-language incident summaries including timeline, assets, and threat actors
- Impact Assessment: Clear visibility into scope, affected entities, and indicators of compromise
- Root Cause Context: Understand how attacks unfolded from initial access to containment
- Natural Language Queries: Ask follow-up questions about incidents Armor is investigating
Script & Malware Analysis
Instant translation of technical malware findings into understandable explanations for non-specialists.
- PowerShell Decoding: Understand what malicious scripts are doing without reverse engineering expertise
- Threat Attribution: See how Armor links script techniques to known threat actors
- IOC Explanation: Comprehend indicators of compromise identified during investigations
- Risk Context: Understand severity and business impact of threats Armor detects
Threat Hunting & Query Generation
Natural language access to security data that enables RWS to explore and validate alongside Armor's hunters.
- Conversational Queries: Ask security questions in plain language, receive meaningful answers
- Query Explanation: Understand the logic behind searches Armor's team performs
- Collaborative Exploration: Investigate specific concerns alongside Armor's threat hunters
- Cross-Platform Visibility: See across Defender XDR, Sentinel, and connected data sources
Autonomous Security Agents
AI agents that accelerate detection and triage, enabling Armor's analysts to focus on complex threats.
- Phishing Triage Agent: Pre-filters email threats, surfacing confirmed risks for Armor review
- Conditional Access Agent: Identifies Zero Trust policy gaps for Armor's recommendations
- Threat Intelligence Briefing: Proactively surfaces emerging threats for Armor's assessment
- Custom Workflows: Armor configures agents aligned to RWS's operational environment
Why this matters for RWS: Security Copilot transforms RWS from a passive consumer of managed security services into an informed, empowered co-management partner. Internal staff can investigate incidents, validate Armor recommendations, and make informed decisions without years of specialized training. This builds institutional security knowledge over time, reduces single-vendor dependency, and ensures RWS leadership can make confident decisions during critical incidents while retaining full operational visibility and control.
Detection & Response Capabilities
Armor's detection and response methodology defines how threats are identified, investigated, and neutralized across RWS's environment. This section details the operational processes and technologies that enable rapid, effective response. Our layered approach combines Microsoft Defender XDR's native capabilities with Armor Nexus's AI-powered enrichment and 15+ years of threat intelligence, ensuring threats are identified across the full attack lifecycle and contained before causing business impact.
Detection Methodology
- Signature-based: Known malware, attack patterns, and IOCs from global threat feeds
- Behavioral Analytics: AI-powered anomaly detection tuned for hospitality and gaming environments
- Threat Intelligence: Commercial and proprietary feeds with dark web monitoring for RWS's industry
- Custom Rules: RWS-specific scenarios developed by Armor's Detection Engineers
- Machine Learning: Microsoft Defender ML combined with Armor tuning for multi-stage attacks
Investigation & Correlation
- AI-Augmented Triage: Automated enrichment delivers 8x faster analysis with confidence scoring
- Cross-Platform Correlation: Links indicators across endpoints, identity, email, and cloud via Defender XDR
- Collaborative Investigation: Armor analysts work directly with RWS IT through shared Nexus dashboards
- Root Cause Analysis: Threat timeline reconstruction with attack chain documentation
- Hunt Summaries: Documented findings and recommendations for every investigation
Response
- AI-Powered Containment: Automated response limits lateral movement within minutes
- RWS-Specific Playbooks: Custom procedures aligned with your change management processes
- Tiered Response Model: Pre-approved actions for immediate containment, escalation paths for business-impacting decisions
- SOAR Integration: Orchestrated workflows connecting Nexus, Defender, and RWS ITSM
- Post-Incident Reporting: Detailed documentation of actions, root cause, and lessons learned
Pre-Approved Response Actions
The following represents our minimum recommended pre-approved containment actions to enable rapid response. Armor maintains a library of additional response actions and can implement customized pre-approved actions tailored to RWS's operational requirements and risk tolerance.
| Action | Trigger | Impact |
|---|---|---|
| Isolate Endpoint | Confirmed malware execution | Device isolated from network, user notified |
| Disable User Account | Confirmed account compromise | Account disabled, sessions terminated |
| Block Hash/Domain | Confirmed malicious indicator | IOC blocked across environment |
| Force Password Reset | Credential theft detected | User required to reset password |
Why this matters for RWS: Every minute between detection and containment increases breach costs and business disruption. Armor's methodology delivers sub-5-minute mean time to detect and containment within minutes of confirmation through AI-powered automation backed by human expertise. Pre-approved response actions eliminate decision delays during critical incidents, while collaborative investigation ensures RWS maintains visibility and control throughout. This combination of speed, precision, and transparency translates directly into reduced downtime, limited blast radius, and faster return to normal operations.
Service Levels & KPIs
Armor's service commitments are designed to ensure rapid threat containment and continuous security effectiveness. These contractual SLAs and measurable KPIs provide RWS with clear accountability, transparent performance tracking, and the confidence that security incidents will be addressed with the urgency they demand.
Response Time SLAs
Armor classifies all security events by severity and commits to defined response and update timelines for each level. These SLAs ensure that critical threats receive immediate attention while maintaining structured workflows for lower-priority events.
| Severity | Definition | Initial Response | Update Frequency |
|---|---|---|---|
| Critical | Active breach, ransomware, critical system compromise | 15 minutes | Every 30 minutes |
| High | Confirmed malware, lateral movement, data exfiltration attempt | 30 minutes | Every 2 hours |
| Medium | Suspicious activity requiring investigation | 2 hours | Every 4 hours |
| Low | Policy violations, informational alerts | 8 hours | Daily |
Key Performance Indicators
Beyond response times, Armor tracks operational KPIs that measure the overall effectiveness and reliability of our security operations.
| KPI | Target | Measurement |
|---|---|---|
| Mean Time to Detect (MTTD) | < 5 minutes | Time from event occurrence to alert generation |
| Mean Time to Respond (MTTR) | < 30 minutes | Time from alert to containment action |
| False Positive Rate | < 10% | Percentage of alerts determined to be benign |
| SLA Compliance | 99.5% | Percentage of incidents meeting response SLAs |
| Platform Availability | 99.9% | Armor Nexus platform uptime |
Why this matters for RWS: These commitments establish clear accountability for security outcomes. Rather than simply providing tools and hoping for the best, Armor contractually commits to detection speed, response times, and operational reliability. RWS gains a partner measured by results, with transparent performance tracking that ensures security investments deliver tangible protection.
Pricing
Our pricing reflects a commitment to delivering enterprise-grade security outcomes at competitive market rates, structured with long-term partnership in mind rather than transactional engagement. This proposal represents significant value through the combination of advanced threat detection capabilities, dedicated security expertise, and continuous advisory services -eliminating the need for substantial in-house investment in specialized talent and technology infrastructure.
We offer two flexible pricing structures to align with your financial planning preferences:
Option 1 – Upfront Implementation provides a single implementation investment at contract signing, resulting in lower ongoing monthly costs throughout the engagement.
Option 2 – Amortized Implementation distributes the implementation investment across the contract term, reducing initial capital outlay while maintaining predictable monthly expenditure.
Both options deliver identical service levels and security outcomes, backed by our commitment to continuous service improvement and collaborative partnership throughout the engagement.
Optional Extension Years (3+1+1)
The following pricing applies to the optional Year 4 and Year 5 extension periods, subject to mutual agreement and written authorization from RWS. Extension pricing reflects continuation of managed services only -no additional implementation fees apply.
| Option Period | Monthly Rate | Annual Total |
|---|---|---|
| Year 4 & Year 5 | $63,837 | $766,044 |
Why This Matters for RWS: This investment replaces the need for multiple full-time security specialists, dedicated SIEM infrastructure, and ongoing training. It delivers immediate operational capability while allowing your internal team to focus on strategic priorities rather than daily security operations. Beyond the numbers, this engagement represents a security partnership designed to mature alongside your organization, with a dedicated team invested in your long-term security posture and business resilience.
Compliance with Tender Specifications
This section maps our solution to the specific requirements outlined in RWS-IT-RFQ-118.
Statement of Compliance
A detailed compliance matrix has been prepared mapping each requirement from the RWS Scope of Work (Appendix B1) to our proposed solution.
Deviations & Exceptions
Content pending
Key Challenges & Risk Areas
Content pending
Project Team
Successful security implementations require experienced professionals with clear ownership and defined accountability. Our team structure spans executive sponsorship through hands-on implementation, with escalation paths that ensure issues are resolved quickly at the appropriate level.
Armor Key Personnel - Implementation
Executive / Strategic Oversight
Chris Drake
Armor Founder & CEO
Technical CSM and Architecture Lead
Karim Wadhwani
Architecture, Implementation, and Operations
Project Manager
TBD
Overall project coordination and delivery
Technical Lead
Jude Antoni
Architecture and technical implementation
Security Architect
Thanapol Balawongse
Security design and integration
Implementation Lead
Malgene Teo
Deployment and configuration
Integration Lead
Vinay Rajput
Technical onboarding and process integration
Escalation Matrix - Phase 1
During implementation, the following escalation structure ensures that project risks, blockers, and decisions are addressed by the right stakeholders without delay.
| Level | RWS Contact | Armor Contact |
|---|---|---|
| Executive | Executive Team | Account Executive |
| Strategic | RWS Project Lead | Project Manager |
| Tactical | RWS Security Architect | Technical Architect |
| Operational | RWS Project Team | Implementation Experts |
Escalation Matrix - Phase 2 (Operations)
Once operational, Armor maintains two parallel escalation paths: one for security incidents requiring technical response, and one for service delivery matters requiring relationship management. This separation ensures security events receive immediate expert attention while service quality issues are addressed through appropriate governance channels.
Technical Escalation
| Level | Trigger | Armor Role | RWS Contact |
|---|---|---|---|
| L1: Auto Triage | Alert fired, SOAR playbooks run | Nexus Platform | Auto-containment |
| L2: Initial Human | Automation cannot resolve or High severity | Security Analyst | Security Team |
| L3: Advanced Analysis | Complex lateral movement or malware | Senior Security Analyst | Security Team Lead |
| L4: Incident Response | Active breach, critical impact | IR Lead | Security Director / CISO |
Service Delivery Escalation
| Level | Trigger | Armor Role | RWS Contact |
|---|---|---|---|
| Functional | Minor SLA delay, report formatting | Customer Success Manager | Security Team Lead |
| Tactical | Recurring issues, missed handoffs | Service Delivery Manager | Security Director |
| Strategic | Critical SLA breach, contractual dispute | Account Executive | Governance Team |
| Executive | Major brand risk, legal/compliance crisis | Chief Risk Officer | Executive Team |
Why this matters for RWS: Clear ownership and defined escalation paths eliminate ambiguity during both implementation and ongoing operations. RWS always knows who to contact, what level of response to expect, and how to escalate when standard channels are insufficient. This structure ensures accountability from day one through the life of the engagement.
Appendices
A. Technical Datasheets
To be attached
B. Architecture Diagrams
Detailed diagrams to be attached
C. Case Studies & References
To be attached
D. Certifications & Accreditations
Certificate copies to be attached
E. Product Roadmap
High-level roadmap to be attached
Disclaimer
- This publication contains proprietary information that is protected by copyright. SoftwareOne reserves all rights thereto.
- SoftwareOne shall not be liable for possible errors in this document. Liability for damages directly and indirectly associated with the supply or use of this document is excluded as far as legally permissible.
- The information presented herein is intended exclusively as a guide offered by SoftwareOne. The publisher's product use rights, agreement terms and conditions and other definitions prevail over the information provided herein. The content must not be copied, reproduced, passed to third parties or used for any other purposes without written permission of SoftwareOne.
- Copyright © by SoftwareOne. All Rights Reserved. SoftwareOne is a registered trademark of SoftwareOne. All other trademarks, service marks or trade names appearing herein are the property of their respective owners.

